Hello and welcome, tech enthusiasts, blockchain explorers, and digital currency pioneers! As we journey together into the complex and captivating realm of blockchain technology, there’s an intriguing conceptual puzzle that we’ll inevitably encounter: the Byzantine Generals Problem. This fascinating theoretical dilemma lies at the heart of digital trust mechanisms, particularly within distributed systems such as blockchain networks. It is critical to understanding how blockchain achieves its unparalleled levels of security, reliability, and robustness in the face of potential threats.
Understanding the Byzantine Generals Problem
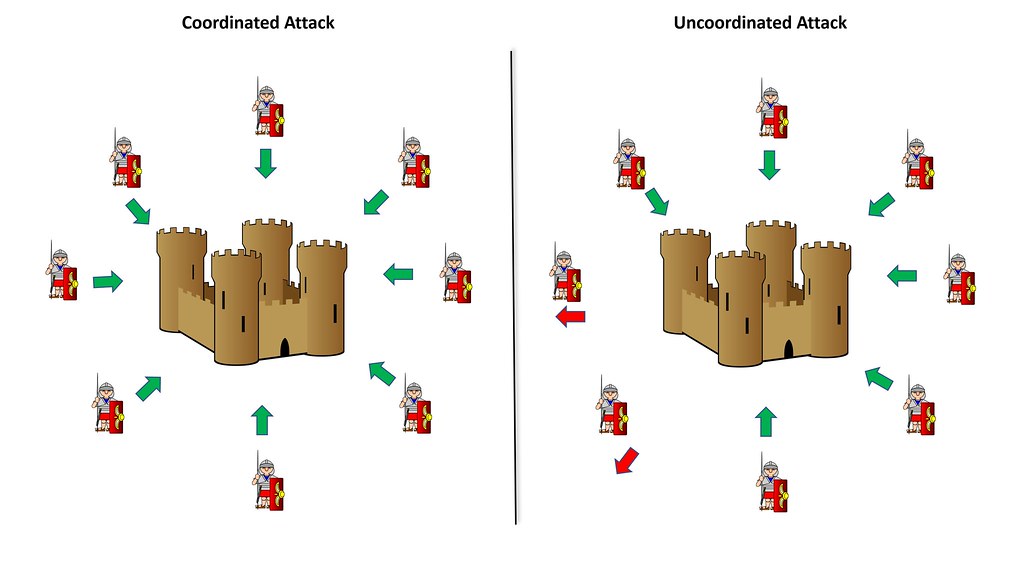

To delve deeper into our exploration, let’s get acquainted with the Byzantine Generals Problem (BGP). In a seminal 1982 paper, computer scientists Leslie Lamport, Robert Shostak, and Marshall Pease presented this hypothetical scenario to illustrate a key challenge in computer systems.
Imagine a group of Byzantine generals planning to attack a fortified city. They can only succeed if they attack simultaneously. However, the generals are located in different places around the city, and their only means of communication is via messengers who may not always be trustworthy. Some generals might even be traitors, passing on false information. Given these complexities, the question is: how can they coordinate their attack to ensure success?
This dilemma mirrors the predicament faced by nodes in a blockchain network. These nodes, like the Byzantine generals, must agree on the legitimacy of transactions despite unreliable communication, potential dishonesty, and absence of a central authority. They require a mechanism to reach consensus while maintaining the network’s security and integrity.
How Blockchain Tackles Dishonest Nodes and Miners
Blockchain networks, much like the Byzantine army, may contain dishonest players. In these networks, nodes and miners could potentially act in dishonest ways to undermine the system.
Dishonest nodes might create a divergence in the set of accepted blocks, leading to inconsistency and instability in the network. To counter this, Bitcoin, one of the most widely known blockchain systems, employs the rule of the longest chain. In the event of a divergence due to rogue nodes, the system accepts the longest chain as the valid one. For a successful attack on the Bitcoin network, an attacker would need to control over 7000 coordinated rogue nodes (as per data of November 2022), an incredibly high barrier to breach.
Likewise, dishonest miners pose a similar threat to the network. These miners might try to include invalid transactions or blocks into the chain, potentially disrupting the system’s integrity. Bitcoin counters this threat through a consensus mechanism called Proof-of-Work (PoW). This system requires miners to solve a complex computational problem to add a block to the blockchain, ensuring that controlling more than 50% of the network’s mining hashrate (a so-called 51% attack) is both computationally difficult and economically unfeasible.
The Role of Hashing in Solving the Byzantine Generals Problem
Hashing, an essential part of the blockchain, plays a vital role in mitigating the Byzantine Generals Problem. But what exactly is hashing?
Hashing is a one-way function that transforms unique plaintext data into a unique, fixed-size string of characters, known as a digest. It’s important to note that it’s practically impossible to derive the original data from the hash digest. Bitcoin, for instance, uses the SHA-256 (Secure Hash Algorithm 256-bit) for this purpose.
Within the context of blockchain, each block’s header is hashed along with a variable value called a nonce to generate a unique hash for that block. Miners must then adjust this nonce repeatedly and recompute the hash until they find one that meets certain requirements. This is the Proof-of-Work (PoW) consensus mechanism.
The blockchain’s immutability comes from the fact that each block header includes the hash of the previous block, effectively creating a chain of blocks that traces back to the first, or ‘genesis’, block. Even a minor change in any block requires re-mining all subsequent blocks, making the blockchain highly resistant to tampering.
Importance of Asymmetric Encryption and Digital Signatures
Another indispensable weapon in blockchain’s arsenal to defeat the Byzantine Generals Problem is asymmetric encryption and digital signatures. Asymmetric encryption, also known as public-key cryptography, involves a pair of mathematically linked keys: a private key, known only to the owner, and a public key, available to everyone.
When a transaction takes place on the blockchain, the sender digitally signs the transaction using their private key. This digital signature verifies the sender’s identity and ensures the integrity of the transaction data. Anyone can confirm the authenticity of this signature using the sender’s public key, but without the private key, the signature can’t be forged.
For example, if Alex wants to send Bitcoin to Bob, Alex uses his private key to sign the transaction. As Alex is the only one with access to his private key, only he can authorize this transaction. Since Alex’s public key is available on the blockchain, anyone can verify the authenticity of the transaction.
Through hashing and asymmetric encryption, blockchain effectively addresses the Byzantine Generals Problem, enabling a transparent, secure, and trustworthy digital infrastructure.
Consensus in Blockchain
The concept of consensus is integral to the functioning of the blockchain network and its capability to solve the Byzantine Generals Problem. Consensus protocols in blockchain ensure that all participating nodes agree on the validity of transactions and the order in which they occur, fostering trust in a decentralized system.
In the Bitcoin network, consensus is achieved through a process called Proof-of-Work (PoW). This involves Bitcoin miners solving complex mathematical problems to find a valid hash for a new block. The first miner to succeed broadcasts the block to the network. Other nodes then verify the solution and, if correct, add the block to their version of the blockchain.
Through the PoW mechanism and a distributed network of nodes, an unfalsifiable cryptographic problem is solved, leading to a common agreement among nodes even in the presence of dishonest participants. It’s this consensus mechanism that allows blockchain networks to overcome the Byzantine Generals Problem, ensuring that even if some nodes fail or act maliciously, the overall system remains secure and operational.
Wrapping Things Up
Solving the Byzantine Generals Problem is a cornerstone of blockchain’s revolutionary potential. By employing robust mechanisms like hashing, asymmetric encryption, digital signatures, and consensus protocols, blockchain ensures that trust, security, and consensus can be maintained in a decentralized environment, even in the face of dishonest actors.
The threats posed by dishonest nodes and miners are significant, but as our exploration shows, they’re systematically addressed within the design of the blockchain network. The robustness of these mechanisms and the sheer computational resources required to subvert them make blockchain an incredibly resilient technology.
Despite these strengths, it’s important to remain cognizant of future risks, such as those potentially posed by quantum computing, and to continue advancing and fortifying blockchain technologies to meet these challenges head-on. The blockchain journey is just beginning, and its true potential is only starting to be realized.